DEFCON 31
I had the opportunity to attend my first DEFCON this year. With work sponsoring my time and receiving a guest pass, the overall expenses were minimal which is what allowed me the opportunity. Next year though, it would probably be better to spend a little more on a hotel.
I chose to stay at the Hilton Grand Vacations Club Paradise Las Vegas. Athough it was considerably cheaper than all of the other locations, it was not without reason. I thought the nearby monorail was closer, but it was actually 0.4-0.5 miles from the hotel. Which, isn’t really that bad - because, you’ll be walking far longer distances at the conference. But walking a round trip distance of a mile in 100F degree heat is not fun.
The admission for the monorail was pretty affordable. I think, for four days it was about $37. And, that covered my entire stay there. It was a lot easier to ride the monorail than to adjust to driving in Las Vegas. To make the trip even easier, I would recommend staying at a hotel directly connected to the monorail station. It was probably $10-20 more a night than my place, but the convenience can’t be beat.
- link: https://www.lvmonorail.com/ (they have maps and digital passes)
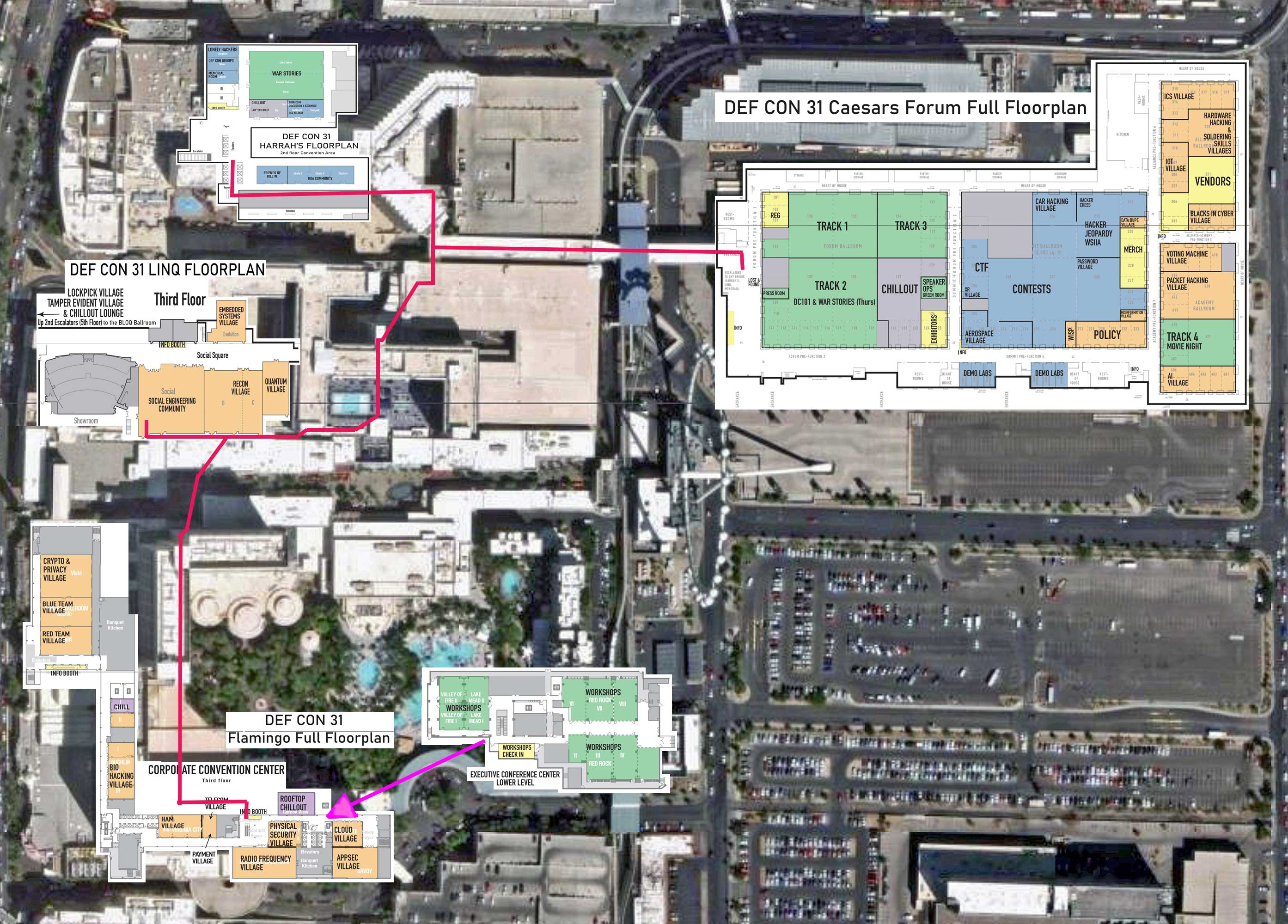
As for actual content of the conference, I got to attend a workshop and several talks. It was really interesting, because you could talk, watch, or partcipate in just about any activity that fits under the “cyber” or “infosec” umbrella. All at varying levels of technical knowledge and skill too; e.g., social engineering village vs embedded devices.
To get all the nitty gritty details, you can just look at the DEFCON 31 Planning forum:
- link: https://forum.defcon.org/node/243392
I managed to explore all of the conference and walked through every village, but the ones most interesting to me were:
- embedded systems
- biohacking
- hardware hacking & soldering skills
- aerospace
- lockpicking
Some of the more popular ones with massive lines were:
- appsec
- blue team
- red team
But, I think that’s because their CTFs were bigger events. Those topics are also just the defaults for cyber/infosec.
As for workshops, see the link:
- https://forum.defcon.org/node/244772
Max Karsten hosted the workshop, “DotNet Malware Analysis Masterclass”, and he graciously allowed me to participate as an “assistant”; he snuck me inside and allowed me to watch, haha. It was really informative and I learned about a couple of new tools for dotnet, other than the defaults included with FlareVM. Apparently, the tools I’ve been using are deprecated and someone forked it; dnSpyEx, de4dot, and DotDumper.
My VM was being wonky, so I didn’t get to participate as well. It wasn’t a great idea trying to run a Windows 10 ARM image with FlareVM within a M1 Macbook; the performance was great for what it was, but there were constant software issues.
For talks, some of the bigger ones that I stayed for were:
- Game-Changing Advances in Windows Shellcode Analysis
- Dr. Bramwell Brizendine, Assistant Professor at UAH
- Jake Hince, Cybersecurity Engineer
- Max ‘Libra’ Kersten, Malware Analyst at Trellix
- Advanced ROP Framework: Pushing ROP to Its Limits
- Dr. Bramwell Brizendine, Assistant Professor at UAH
- Shiva Shashank Kusuma, Computer Science Master’s student at UAH
Both really interesting and highly technical. I think the content is worth digesting if you want to build more advanced windows exploits.
There was a bunch more that happened, like eating at an italian place with the group, some hacker parties, buying lockpicking sets, and even a bomb/”suspicious package” threat. But, this blog post is plenty long enough as is.
